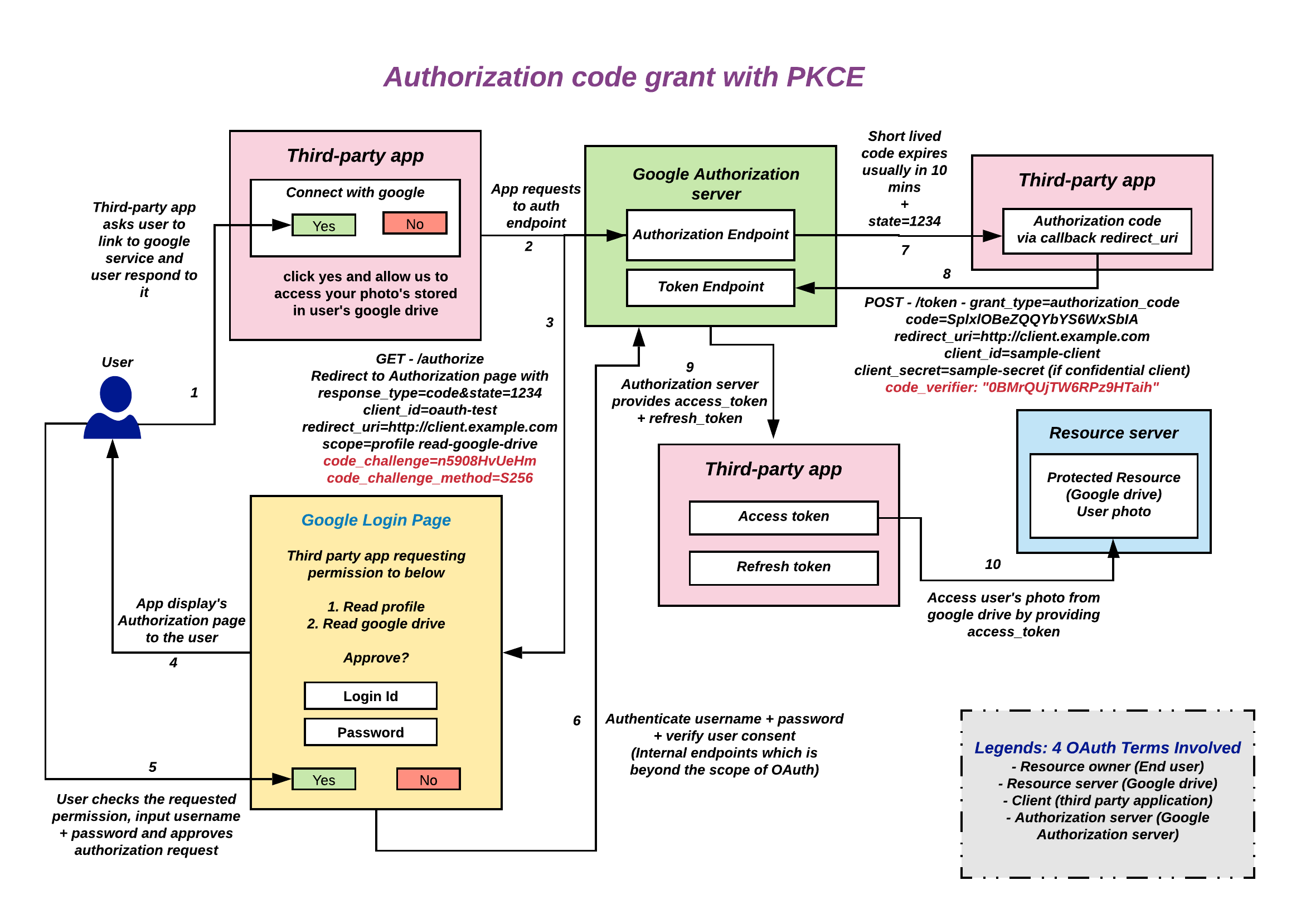
# Authentication --- #### JWT 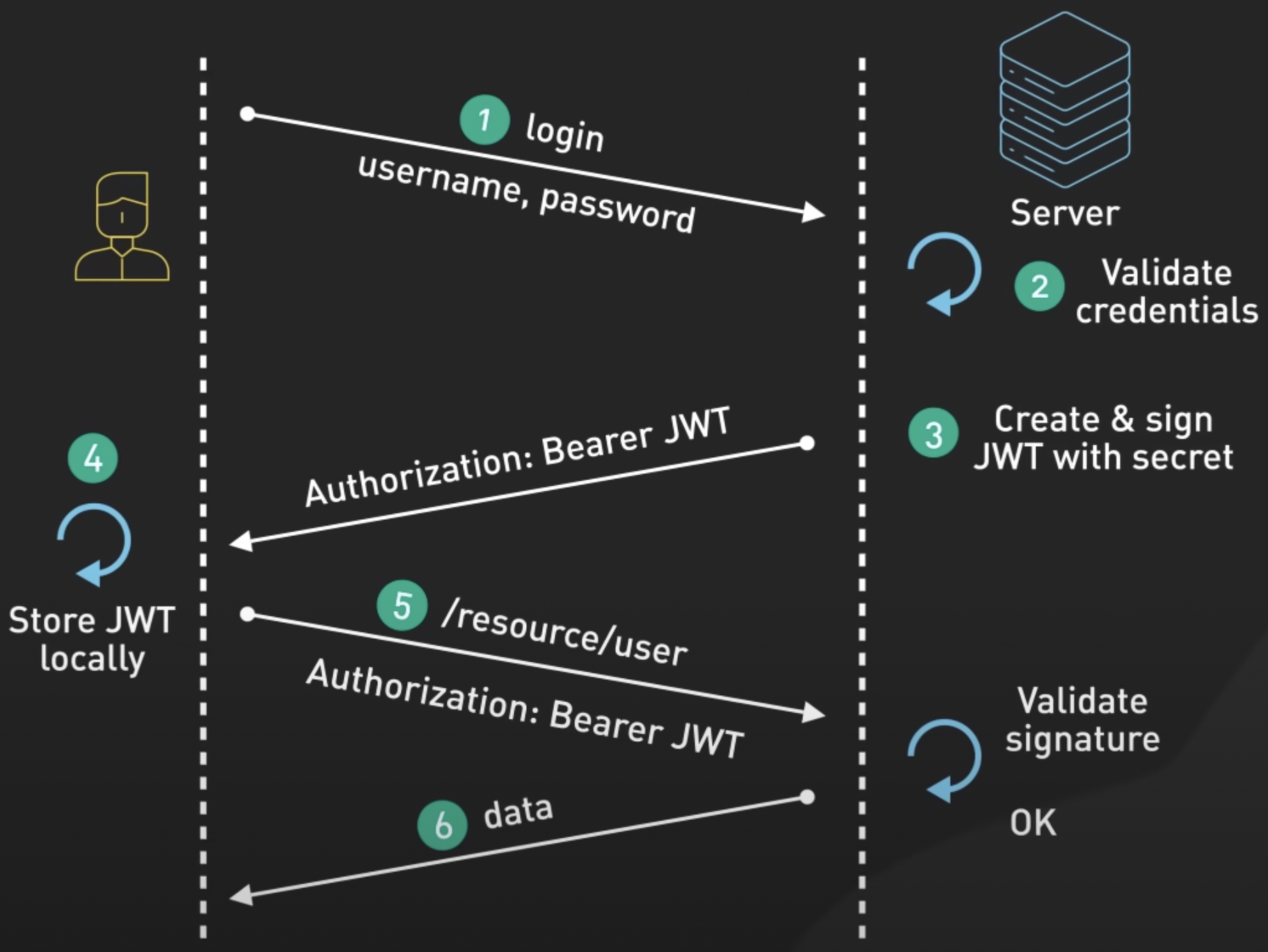 <!-- .element: class="r-stretch" --> ---- #### Token 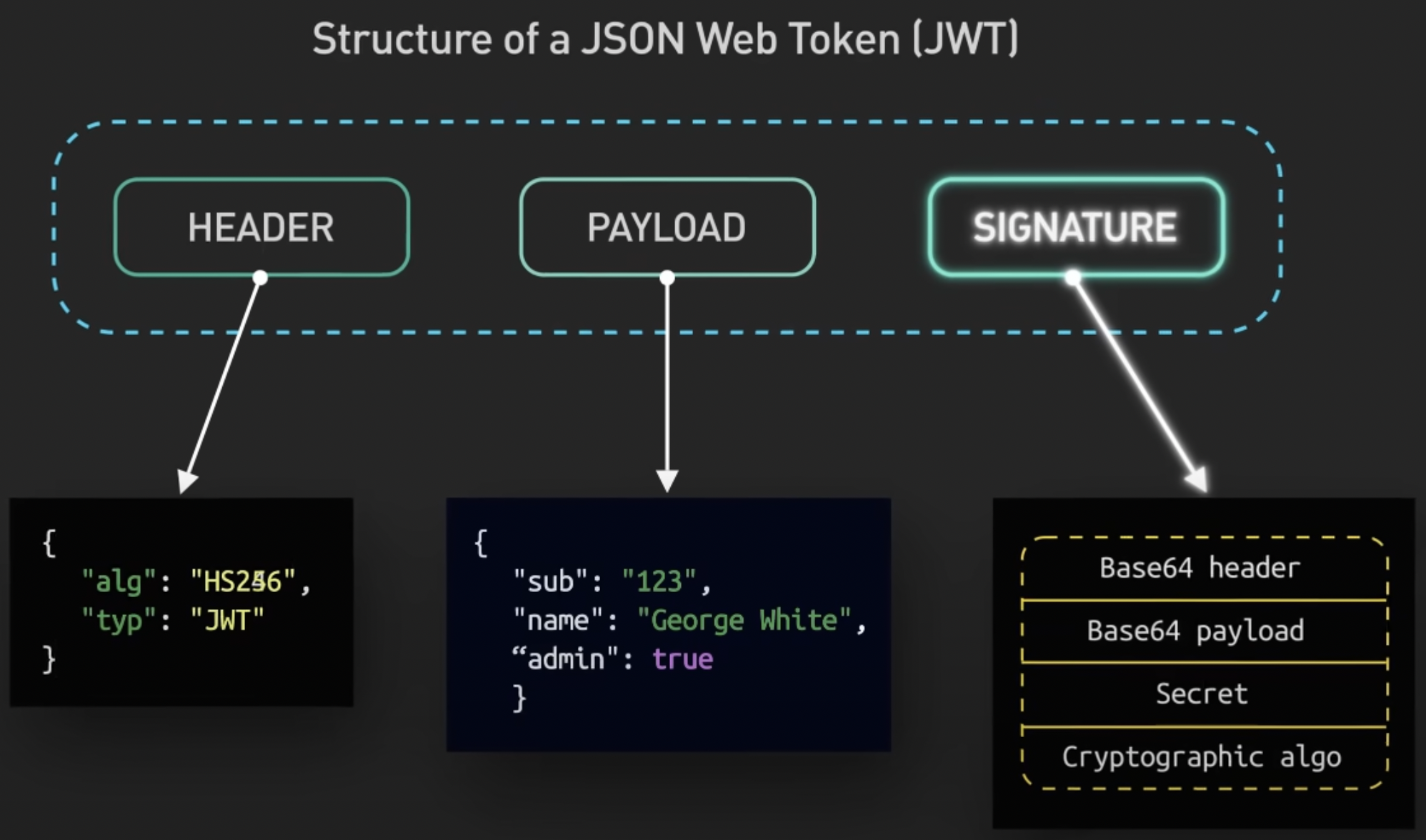 <!-- .element: class="r-stretch" --> ---- #### `login`/`logout` ```typescript login(username: string, password: string) { return this.httpClient .post<{ token: string }>(`${this.baseUrl}/token`, { username: username, password: password }) .pipe( tap(response => { localStorage.setItem(AuthService.tokenKey, response.token); this._user.set(username); }) ); } ``` <!-- .element: class="stretch fragment" --> ```typescript logout(): void { localStorage.removeItem(AuthService.tokenKey); this._user.set(''); this.router.navigate(['/login']); } ``` <!-- .element: class="stretch fragment" --> ---- #### Interceptor ```typescript export const authInterceptor: HttpInterceptorFn = (req, next) => { const authService = inject(AuthService); if (!authService.isLoggedIn()) return next(req); const cloned = req.clone({ headers: req.headers.set('Authorization', `Bearer ${authService.getToken()}`) }); return next(cloned); }; ``` <!-- .element: class="stretch fragment" --> --- #### OAuth  ---- #### Flow 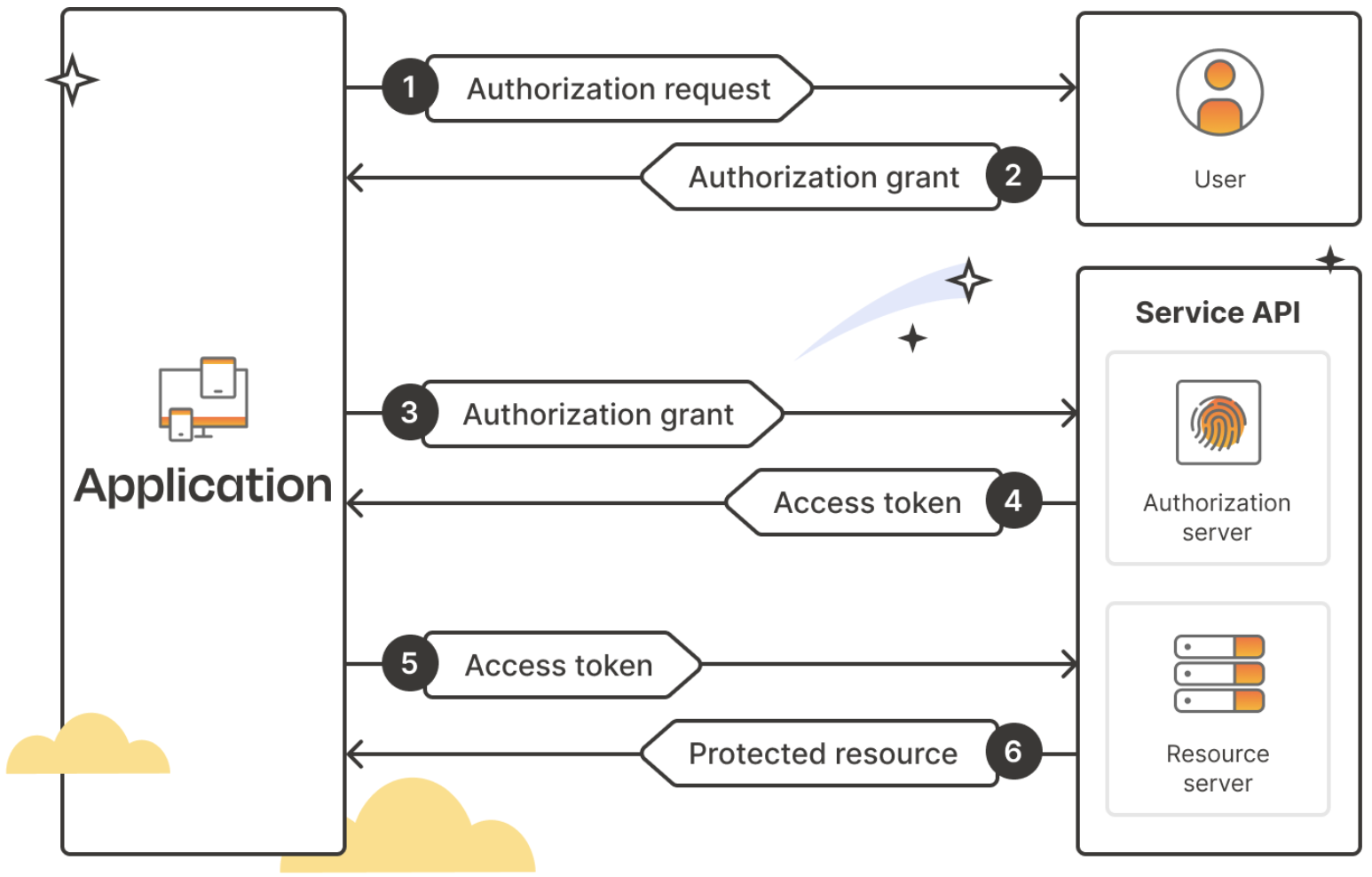 note: warum nicht gleich den token? Apps könnten Browser-URL mitlesen ---- #### Vorteile * beschränkte Rechte <!-- .element: class="fragment fade-in-then-semi-out" --> * Passwort bleibt beim Authentication-Service <!-- .element: class="fragment fade-in-then-semi-out" --> * Single-Sign-On <!-- .element: class="fragment fade-in-then-semi-out" --> * SRP - unterschiedliche Services für auth und Dienste <!-- .element: class="fragment fade-in-then-semi-out" --> * Jederzeit widerrufbar <!-- .element: class="fragment fade-in" --> --- #### Intercept Attack 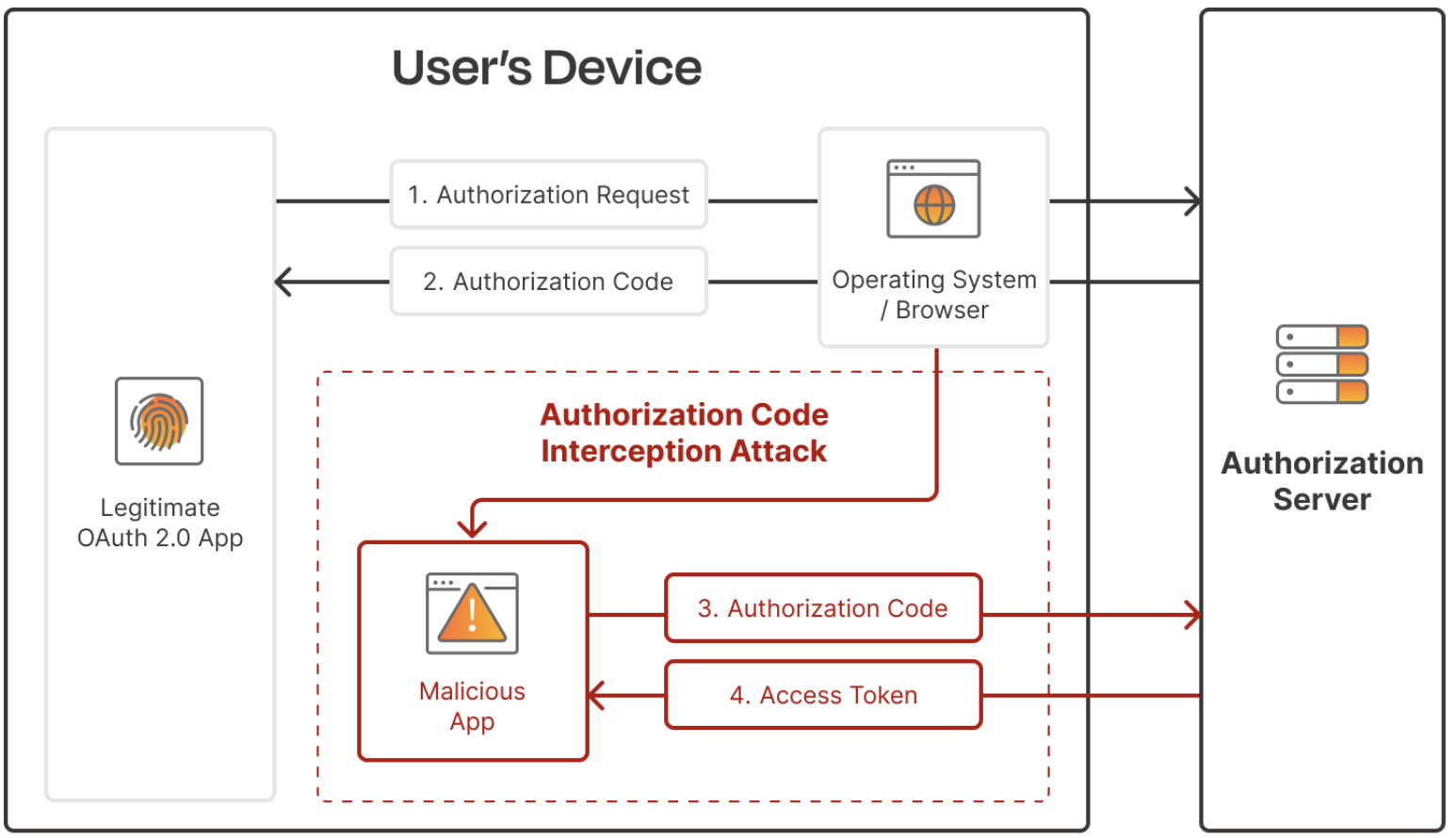 ---- #### PKCE 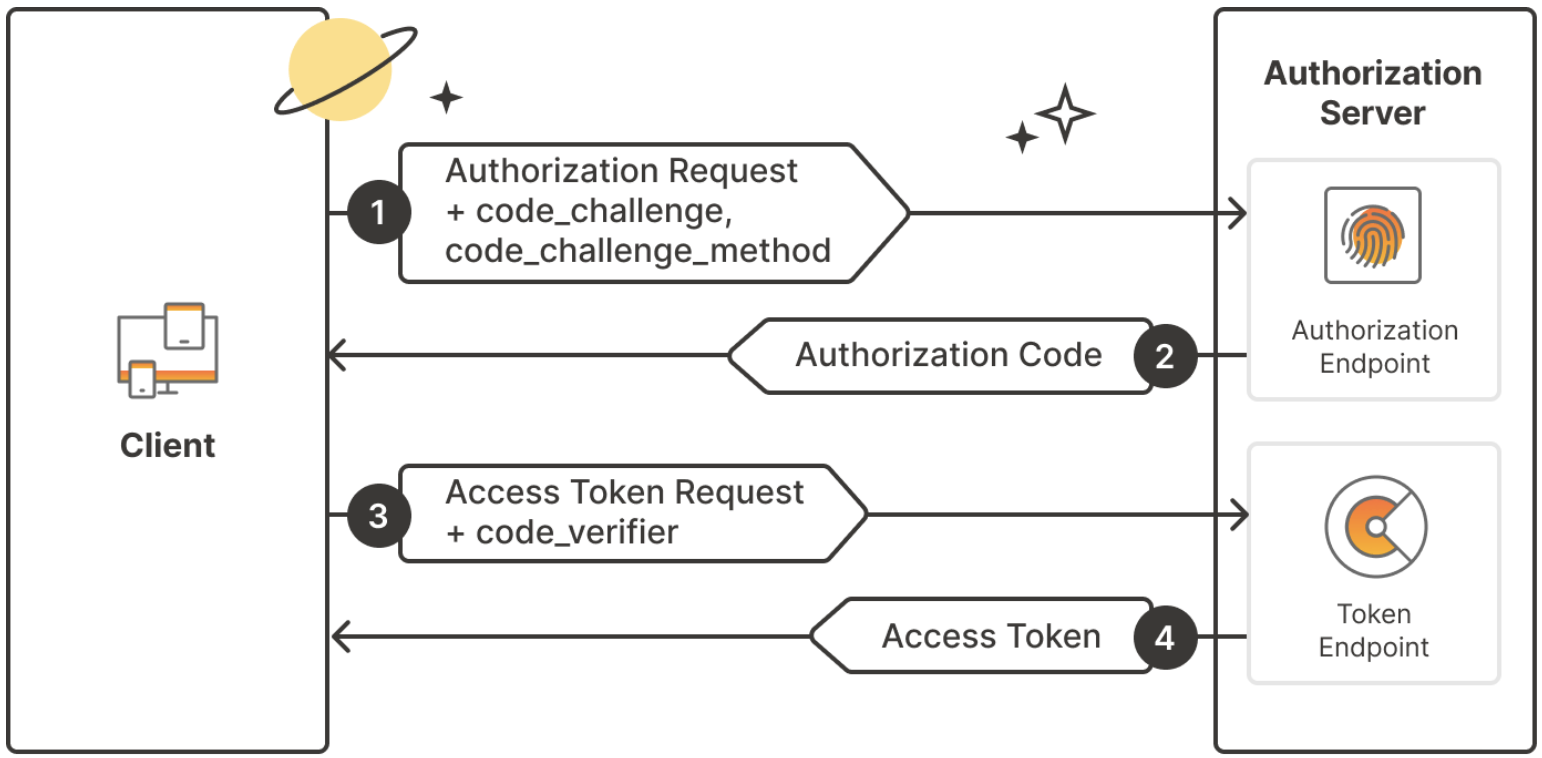 <!-- .element: style="height:7em" --> ```python code_verifier = get_random_string() code_challenge = SHA256(code_verifier) ``` <!-- .element: class="fragment stretch" --> ```http request GET /authorize? client_id=...&scope=...&response_type=code&redirect_uri=target& code_challenge=base64url(code_challenge)& code_challenge_method=S256 ``` <!-- .element: class="fragment stretch" --> ```http request POST /token client_id=...&redirect_uri=...&code=acode&code_verifier=verifier ``` <!-- .element: class="fragment stretch" --> ----